title: "Affaire Azure"
date: 2023-08-03
id: 20231011171736Affaire Azure
An Azure weakness allow chinese hackers to steal a security key later used to forge access tokens to various MS services. Many customers were not able to detect it because their licences does not provide access to security logs. Under pressure, MS now "gives" access to theses logs to all (? ) customers.
tags : #area/watch
source :Microsoft comes under blistering criticism for “grossly irresponsible” security | Ars Technica
date : 2023-08-03
“What you hear from Microsoft is ‘just trust us,’ but what you get back is very little transparency and a culture of toxic obfuscation,” he wrote. “How can a CISO, board of directors or executive team believe that Microsoft will do the right thing given the fact patterns and current behaviors? Microsoft’s track record puts us all at risk. And it’s even worse than we thought.”
tags : #area/watch
source :US senator blasts Microsoft for “negligent cybersecurity practices” | Ars Technica
date : 2023-07-28
[..] details Microsoft has disclosed so far lead to the inescapable conclusion that vulnerabilities in code for Azure AD and other cloud offerings were exploited to pull off the successful hack. [...]
weakness allowed the attackers to acquire an expired Microsoft Account encryption key that’s used to log consumers into Exchange accounts.
Ron Wyden ( [.. ]He accused Microsoft of hiding the role it played in the SolarWinds supply chain attack
from comments :
Ron Wyden is literally the only member of Congress worth listening to on tech issues. He's the only one who's shown even passing understanding of Section 230 or Net Neutrality, and has been consistently the voice of reason when it comes to technology in the US. He was also outspoken against the PATRIOT Act (and the warrantless surveillance of US citizens that it enabled) as early as 2006.
tags : #area/watch #china #microsoft #azure
source : Stolen Microsoft key may have opened up more than inboxes • The Register
Microsoft takes pains to obscure role in 0-days that caused email breach | Ars Technica
Azure AD Token Forging Technique in Microsoft Attack Extends Beyond Outlook, Wiz Reports (thehackernews.com)
Microsoft makes cloud security logs available for free • The Register
date : 2023-07-24
A stolen Microsoft security key may have allowed Beijing-backed spies to break into a lot more than just Outlook and Exchange Online email accounts.
Incredibly as it sounds, and it really does deserve wider coverage, someone somehow obtained one of Microsoft's internal private cryptographic keys used to digitally sign access tokens for its online services. With that key, the snoops were able to craft tokens to grant them access to Microsoft customers' email systems and, crucially, sign those access tokens as the Windows giant to make it look as though they were legitimately issued.
With those golden tokens in hand, the snoops – believed to be based in China – were able to log into Microsoft cloud email accounts used by US government officials, including US Commerce Secretary Gina Raimondo. The cyber-trespassing was picked up by a federal government agency, which raised the alarm.
Microsoft still, to the best of our knowledge, does not know (or isn't publicly saying yet) how this incredibly powerful private signing key was obtained, and has revoked that key.
Here are some quick links
- Microsoft's analysis of the espionage involving these, as it put it, forged access tokens signed by its MSA key. Microsoft dubbed the spiesStorm-0558.
- US government leans on Redmond to make cloud security logs available for free in the wake of this fiasco.
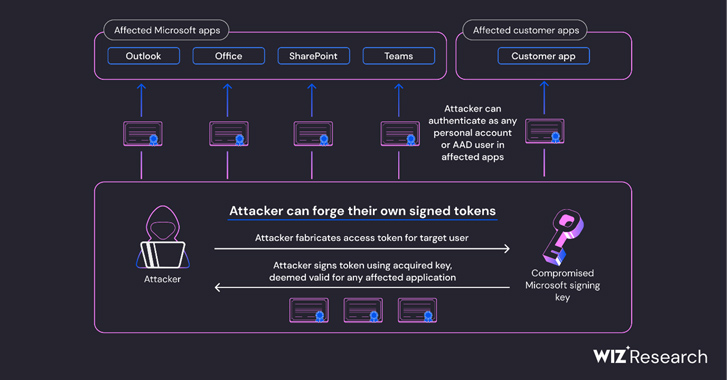
"Our researchers concluded that the compromised MSA key could have allowed the threat actor to forge access tokens for multiple types of Azure Active Directory applications," Tamari explained on Friday.
This includes Microsoft applications using OpenID v2.0 access tokens for account authentication, such as Outlook, SharePoint, OneDrive, and Teams, we're told.
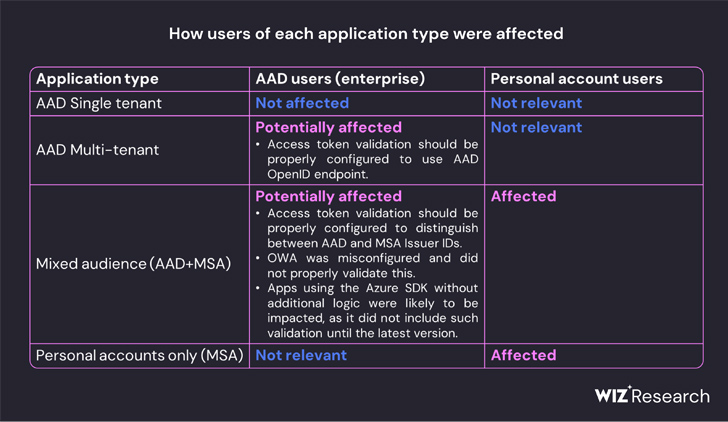
Also, according to Wiz, it spans customers' own applications that support the "login with Microsoft" functionality, plus multi-tenant applications configured to use the "common" v2.0 keys endpoint instead of the "organizations" one. Applications using OpenID v1.0 remain safe.
Still, while Microsoft revoked the compromised encryption key and published a list of indicators-of-compromise for those wondering if they've also been hit by Storm-0558, the Wiz kids said it may be difficult for Redmond's customers to know if miscreants used forged tokens to steal data from their applications. Tamari blamed this on the lack of logs related to token verification.
And, it just so happens that Redmond on Wednesday caved to pressure from the US government agreed to provide all customers with free access to cloud security logs – a service usually reserved for premium clients – but not until September.
According to the Wiz security team, the China-based crew looks to have obtained one of several keys used for verifying Azure Active Directory (AAD) access tokens, allowing them to sign as Microsoft any OpenID v2.0 access token for personal accounts along with multi-tenant and personal-account AAD applications.
While Microsoft pulled the compromised key, meaning it can no longer be used to forge tokens and access AAD applications, there's a chance that during previously established sessions attackers could have used this access to deploy backdoors or otherwise establish persistence.
"A notable example of this is how, prior to Microsoft's mitigation, Storm-0558 issued valid Exchange Online access tokens by forging access tokens for Outlook Web Access (OWA)," Tamari wrote.
Additionally, applications that use local certificate stores or cached keys may still trust the compromised key and thus be vulnerable to attack. Because of this, both Wiz and Microsoft urge refreshing those silos at least once a day. ®
Azure AD Token Forging Technique in Microsoft Attack Extends Beyond Outlook, Wiz Reports
_Jul 21, 2023_THNEmail Security / Cyber Attack
According to cloud security company Wiz, the inactive Microsoft account (MSA) consumer signing key used to forge Azure Active Directory (Azure AD or AAD) tokens to gain illicit access to Outlook Web Access (OWA) and Outlook.com could also have allowed the adversary to forge access tokens for various types of Azure AD applications.
This includes every application that supports personal account authentication, such as OneDrive, SharePoint, and Teams; customers applications that support the "Login with Microsoft functionality," and multi-tenant applications in certain conditions.
"Everything in the world of Microsoft leverages Azure Active Directory auth tokens for access," Ami Luttwak, chief technology officer and co-founder of Wiz, said in a statement. "An attacker with an AAD signing key is the most powerful attacker you can imagine, because they can access almost any app – as any user. This is a 'shape shifter' superpower."
Wiz's analysis fills in some of the blanks, with the company discovering that "all Azure personal account v2.0 applications depend on a list of 8 public keys, and all Azure multi-tenant v2.0 applications with Microsoft account enabled depend on a list of 7 public keys."
It further found that Microsoft replaced one of the the listed public keys (thumbprint: "d4b4cccda9228624656bff33d8110955779632aa") that had been present since at least 2016 sometime between June 27, 2023, and July 5, 2023, around the same period the company said it had revoked the MSA key.
"This led us to believe that although the compromised key acquired by Storm-0558 was a private key designed for Microsoft's MSA tenant in Azure, it was also able to sign OpenID v2.0 tokens for multiple types of Azure Active Directory applications," Wiz said.
"Storm-0558 seemingly managed to obtain access to one of several keys that were intended for signing and verifying AAD access tokens. The compromised key was trusted to sign any OpenID v2.0 access token for personal accounts and mixed-audience (multi-tenant or personal account) AAD applications."
This effectively meant that the loophole could theoretically enable malicious actors to forge access tokens for consumption by any application that depends on the Azure identity platform.
Even worse, the acquired private key could have been weaponized to forge tokens to authenticate as any user to an affected application that trusts Microsoft OpenID v2.0 mixed audience and personal-accounts certificates.
"Identity provider's signing keys are probably the most powerful secrets in the modern world," Wiz security researcher Shir Tamari said. "With identity provider keys, one can gain immediate single hop access to everything, any email box, file service, or cloud account."
Microsoft Expands Cloud Logging to Counter Rising Nation-State Cyber Threats
_Jul 20, 2023_THNCloud Security / Cyber Espionage
Microsoft on Wednesday announced that it's expanding cloud logging capabilities to help organizations investigate cybersecurity incidents and gain more visibility after facing criticism in the wake of a recent espionage attack campaign aimed at its email infrastructure.
The tech giant said it's making the change in direct response to increasing frequency and evolution of nation-state cyber threats. It's expected to roll out starting in September 2023 to all government and commercial customers.
"Over the coming months, we will include access to wider cloud security logs for our worldwide customers at no additional cost," Vasu Jakkal, corporate vice president of security, compliance, identity, and management at Microsoft, said. "As these changes take effect, customers can use Microsoft Purview Audit to centrally visualize more types of cloud log data generated across their enterprise."
As part of this change, users are expected to receive access to detailed logs of email access and more than 30 other types of log data previously only available at the Microsoft Purview Audit (Premium) subscription level. On top of that, the Windows maker said it's extending the default retention period for Audit Standard customers from 90 days to 180 days.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) welcomed the move, stating "having access to key logging data is important to quickly mitigating cyber intrusions" and that it's "a significant step forward toward advancing security by design principles."
The development comes in the aftermath of disclosures that a threat actor operating out of China, dubbed Storm-0558, breached 25 organizations by exploiting a validation error in the Microsoft Exchange environment.
The U.S. State Department, which was one among the affected entities, said it was able to detect the malicious mailbox activity in June 2023 due to enhanced logging in Microsoft Purview Audit, specifically using the MailItemsAccessed mailbox-auditing action, prompting Microsoft to investigate the incident.
But other impacted organizations said they were unable to detect that they were breached because they were not subscribers of E5/A5/G5 licenses, which come with elevated access to various kinds of logs that would be crucial to investigate the hack.
Attacks mounted by the actor are said to have commenced on May 15, 2023, although Redmond said that the adversary has displayed a propensity for OAuth applications, token theft, and token replay attacks against Microsoft accounts since at least August 2021.
Microsoft, in the meanwhile, is continuing to probe the intrusions, but to date the company hasn't explained how the hackers were able to acquire an inactive Microsoft account (MSA) consumer signing key to forge authentication tokens and obtain illicit access to customer email accounts using Outlook Web Access in Exchange Online (OWA) and Outlook.com.
"The objective of most Storm-0558 campaigns is to obtain unauthorized access to email accounts belonging to employees of targeted organizations," Microsoft revealed last week.
"Once Storm-0558 has access to the desired user credentials, the actor signs into the compromised user's cloud email account with the valid account credentials. The actor then collects information from the email account over the web service."
Microsoft takes pains to obscure role in 0-days that caused email breach
Critics also decry Microsoft's "pay-to-play" monitoring that detected intrusions.
On Friday, Microsoft attempted to explain the cause of a breach that gave hackers working for the Chinese government access to the email accounts of 25 organizations—reportedly including the US Departments of State and Commerce and other sensitive organizations.
In a post on Friday, the company indicated that the compromise resulted from three exploited vulnerabilities in either its Exchange Online email service or Azure Active Directory, an identity service that manages single sign-on and multifactor authentication for large organizations. Microsoft’s Threat Intelligence team said that Storm-0558, a China-based hacking outfit that conducts espionage on behalf of that country’s government, exploited them starting on May 15. Microsoft drove out the attackers on June 16 after a customer tipped off company researchers of the intrusion.
Above all else: Avoid the Z-word
In standard parlance among security professionals, this means that Storm-0558 exploited zero-days in the Microsoft cloud services. A “zero-day” is a vulnerability that is known to or exploited by outsiders before the vendor has a patch for it. “Exploit” means using code or other means to trigger a vulnerability in a way that causes harm to the vendor or others.
While both conditions are clearly met in the Storm-0558 intrusion, Friday’s post and two others Microsoft published Tuesday, bend over backward to avoid the words “vulnerability” or “zero-day.” Instead, the company uses considerably more amorphous terms such as “issue,” “error,” and “flaw” when attempting to explain how nation-state hackers tracked the email accounts of some of the company's biggest customers.
“In-depth analysis of the Exchange Online activity discovered that in fact the actor was forging Azure AD tokens using an acquired Microsoft account (MSA) consumer signing key,” Microsoft researchers wrote Friday. “This was made possible by a validation error in Microsoft code.”
Later in the post, the researchers said that Storm-0558 acquired an inactive signing key used for consumer cloud accounts and somehow managed to use it to forge tokens for Azure AD, a supposedly fortified cloud service that, in effect, stores the keys that thousands of organizations use to manage logins for accounts on both their internal networks and cloud-based ones.
“The method by which the actor acquired the key is a matter of ongoing investigation,” the post stated. “Though the key was intended only for MSA accounts, a validation issue allowed this key to be trusted for signing Azure AD tokens.”
Two paragraphs later, Microsoft said that Storm-0558 used the forged token to gain access to Exchange email accounts through a programming interface for Outlook Web Access (OWA). The researchers wrote:
Once authenticated through a legitimate client flow leveraging the forged token, the threat actor accessed the OWA API to retrieve a token for Exchange Online from the GetAccessTokenForResource API used by OWA. The actor was able to obtain new access tokens by presenting one previously issued from this API due to a design flaw. This flaw in the GetAccessTokenForResourceAPI has since been fixed to only accept tokens issued from Azure AD or MSA respectively. The actor used these tokens to retrieve mail messages from the OWA API.
A plain-English summary of the event would seem to be: Microsoft has patched three vulnerabilities in its cloud service that were discovered after Storm-0558 exploited them to gain access to customer accounts. It would also be helpful if Microsoft provided a tracking designation under the CVE (Common Vulnerabilities and Exposures) system the way other cloud companies do. So why doesn’t Microsoft do the same?
“I don't think Microsoft ever acknowledges vulnerabilities in their cloud services (also there's no CVEs for cloud), and you don't say breach at Microsoft,” independent researcher Kevin Beaumont said on Mastodon. “They did say ‘exploit’ in the original MSRC blog in relation to Microsoft's cloud services, and you exploit a vulnerability. So I think it's fair to say that, yes, they had vuln(s).”
Microsoft issued the following comment: "We don’t have any evidence that the actor exploited a 0day." Microsoft didn't elaborate. In one of the two posts published on Tuesday, Microsoft said: "The actor exploited a token validation issue to impersonate Azure AD users and gain access to enterprise mail." Ars has asked for clarification of exactly what was exploited by the threat actor.
Pay-to-play security
Besides being opaque about the root cause of the breach and its own role in it, Microsoft is under fire for withholding details that some of the victims could have used to detect the intrusion, something critics have called “pay-to-play security.” According to the US Cybersecurity and Information Security Agency, one federal agency that was breached by Storm-0558, it discovered the intrusion through audit logs that track logins and other important events affecting customers’ Microsoft cloud accounts.
Microsoft, however, requires customers to pay an additional fee to access these records. The cost for an “E5” enterprise license allowing such access is $57 per month per user, compared to an E3 license cost of $36 per month per customer.
“The fact that Microsoft only allows those who pay the extra money for E5 licensing to see the relevant log files is, well, something…” Will Dorman, senior principal analyst at Analygence, said in an interview. “If you're not an E5-paying customer, you lose the ability to see that you were compromised.”
While Microsoft’s disclosures have been less than forthcoming in the role its vulnerabilities played in breaching the accounts of organizations, Friday’s disclosure provides helpful indicators that people can use to determine if they’ve been targeted or compromised by Storm-0558.